Rival companies and governments may use illegal tactics to spy and steal sensitive information. Whether committed by a spiteful staff member, malicious plant or external hacker, corporate espionage can cause irreparable reputational and financial damage to your organisation.
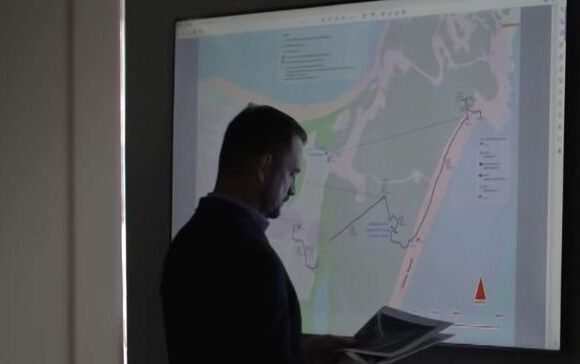
IFW investigators and intelligence operatives work covertly and in close alignment with government bodies, law enforcement agencies and multinational corporations to uncover this crime. We conduct surveillance operations, investigations and cyber intelligence to identify and mitigate potential threats and security risks in real time.
Gathering evidence and intelligence on potential threats to an entity and its personnel, we have caused the successful arrest and prosecution of offenders involved in corporate espionage in numerous foreign jurisdictions. Contact us now to bring the truth to light and take legal action if required.
As featured on
What is corporate espionage?
Also known as industrial or economic espionage, Corporate espionage occurs when trade secrets or intellectual property are stolen from one organisation and given to another. Examples of stolen information include trade policies, research reports, customer data, financial insights and market strategies.
Driven by greed or malice, unauthorised intelligence gathering can be committed by insiders such as a disgruntled employee or external entities like a competitor.
At IFW Global, we are on a mission to crack down on corporate espionage and the criminals behind it. To start your investigation, contact our expert team today.
The consequences of corporate espionage
Loss of competitive advantage
A business may hold exclusive knowledge that is central to the opportunity’s value. If a competitor gets its hands on such insights through spying or theft, this original leg up is lost.
Lack of innovation
Corporate espionage negates the competitive market that is inherent to innovation and growth. Instead of inventing progressively better solutions, businesses steal to deliver the exact same offering.
Security expenses
With corporate espionage posing a real threat to modern-day businesses, companies often have no choice but to invest in deploying several layers of security defence.
Legal penalties
If sensitive information that should have been protected by strict regulations is stolen in an act of corporate espionage, the target company faces significant legal penalties for non-compliance.
Reputational damage
The long-term reputational damage associated with failure to protect personal data can be fatal to an organisation, especially if customers switch to a competitor with superior security measures.
Corporate espionage investigators with a proven track record
Licenced investigators
With backgrounds spanning law enforcement, foreign intelligence, military special forces and corporate security, our licenced operatives are highly skilled in corporate espionage investigations.
Lawful evidence
We will provide you with a concise investigation report including photographs and/or video footage that have been obtained legally. This helps to ensure that any evidence gathered is admissible in Court, equipping you to take corrective action if desired.
Dynamic strategies
IFW uses tailored techniques and sophisticated electronic equipment to collect real-world evidence and intelligence. When authorised, additional technical resources such as lawful tracking devices may be used to gain successful outcomes.
Worldwide resources
Our corporate espionage investigators can gather actionable intelligence in practically any foreign jurisdiction. We leverage open-source intelligence capabilities, direct access to state and federal databases and strategic relationships with law enforcement agencies.
Utmost discretion
Client privacy is paramount, which is why IFW keeps all case details confidential unless disclosed with your consent. When performing an investigation, we ensure all personal data is securely filed, encrypted and stored.
Exceptional results
With an extensive portfolio showcasing successful outcomes, IFW investigators are retained by international law firms, multinational corporations, foreign government agencies, high-net-worth individuals, major television networks and digital media.
Frequently asked questions
Top-
Competitive intelligence differs from corporate espionage in that it does not involve the theft of trade secrets – a business takes advantage of publicly available resources, such as websites, news articles, product purchases and patent filings, to analyse its competitors. In contrast, corporate espionage aims to steal private, proprietary information through illicit activities.
-
The two main types of corporate espionage are intellectual property acquisition and trade secret theft.
Intellectual property acquisition, or IP theft, involves stealing innovative inventions or novel information from a business for financial or other gains. Examples of information that may be targeted include manufacturing processes, customer data, product research and development, company policies and marketing strategies.
Meanwhile, a trade secret refers to any private information with potential economic value to the business that owns it. As workers produce and share trade secrets online on a frequent basis, they are particularly challenging to protect. Emails, browser histories, cloud platforms and other day-to-day business tools can all hold sensitive information that is vulnerable to malware attacks.
-
Corporate espionage tends to stem from within a business. These crimes are most often committed by a disgruntled employee, planted spy or business partnership set up with the purpose of gathering intelligence. Such entities take advantage of human connections to collect sensitive information that could ultimately be used to your company’s detriment.
-
There are multiple ways to commit corporate espionage. However, the most common strategies include:
- Unauthorised access occurs when the culprit accesses networks, data, devices or applications without consent to exploit or destroy certain systems.
- Phishing attacks target victims with emails that feature a fraudulent document or link that seems legitimate. In reality, this content is designed to entice users to take action that gives the attacker information or access to a specific system.
- SQL injections use code to control backend databases and gain access to private information. Attackers may then monitor or modify the database as desired.
- Insider threats may be due to human error or malintent. These users usually have authorised access to key information, making such risks infamously challenging to prevent.
-
Yes, corporate espionage is a criminal offence. While it is not illegal to obtain publicly accessible information, obtaining trade secrets or intellectual property without consent is usually prohibited.
-
Your business should follow the below best practices to prevent corporate espionage:
Create an acceptable use policy
Lack of knowledge about appropriate data-sharing practices makes information susceptible to corporate espionage. Therefore, it’s important to establish policies that inform staff on proper data handling. To ensure everyone is aware of access restrictions, these guidelines must be readily accessible to all employees, contractors, and associated third parties.
You might also consider applying the Principle of Least Privilege to limit access rights for all staff members. Implementing Attribute-Based Access Control (ABAC) within your Identity and Access Management (IAM) framework can help to guarantee that employees only have access to the information required for their roles.
Stay on top of data security
Implement comprehensive encryption for confidential business data, particularly that which is stored in the cloud and shared via the internet. Formulate a solid disaster recovery plan to maintain business operations in the face of a ransomware attack.
Implement network and physical security measures
Restrict on-site data centre access to those with authorisation to ensure sensitive company information housed on servers is protected. Keep a vigilant eye on your IT infrastructure for any unusual actions.
Educate and incentivise all staff members
Everyday activities of your employees involve the handling of sensitive corporate information, which may result in data being compromised or leaked, regardless of intent. For example, the pursuit of efficiency may lead to the use of technology that can heighten the risk of corporate espionage.
Therefore, your security infrastructure should discern between accidental and intentional security breaches and facilitate an appropriate response. The goal is to foster a culture of collaboration without compromising on security or hindering productivity.
Above all, cultivate a workforce environment that prioritises people and places a premium on cyber security diligence. It is essential to educate your team about the implications of corporate espionage for the company’s prospects, the broader market, and their professional development.
Perform regular risk assessments
Threat levels fluctuate, making it crucial to consistently re-examine your company’s risk profile. Detailed evaluations are instrumental in recognising the principal sources of threats, the potential impact on essential operations, and the efficacy of existing risk mitigation strategies.
Understanding your organisation’s strengths and vulnerabilities enables you to make strategic improvements to safeguard its information.
-
The cost of an investigation into corporate espionage varies according to the complexity of your case. At IFW, our investigative services are charged at an hourly fee, plus travel expenses and a kilometre rate.
Once your budget has been confirmed, IFW will recommend an investigation package to determine the amount of hours required to achieve your objectives.
-
The duration of a corporate espionage investigation will depend on your budget and the circumstances of the case in question.
For further information tailored to your case, please contact our investigators today.
-
Generally, evidence of corporate espionage may be used in a Court case if it has been obtained legally.









 Philippines National Police
Philippines National Police  Californian Association of Licensed Investigators
Californian Association of Licensed Investigators  NSW Police Force
NSW Police Force  Philippine Securities and Exchange Commission
Philippine Securities and Exchange Commission 